Our zero trust maturity model assessment is an essential service tailored for government programs and large organizations. In just 12 weeks, we provide a clear, actionable roadmap aligned with DoD ZTA COA standards. This comprehensive evaluation pinpoints your current maturity level, identifies gaps, and helps prioritize steps for maximum impact. Start your journey towards enhanced security and operational clarity today with quarterly progress tracking.
Who This Is For
-
Government agencies & large organizations
-
Federal primes & partners
-
CISOs and Zero Trust program leads
-
Cyber directors and program executives
-
Security and architecture leaders driving Zero Trust implementation
Typical triggers
-
Government agencies & large organizations
-
Federal primes & partners
-
CISOs and Zero Trust program leads
-
Cyber directors and program executives
-
Security and architecture leaders driving Zero Trust implementation
The Problem We Keep Seeing
Zero Trust programs are stumbling, going over budget, failing to meet ROI goals, or not producing tangible results usually for one or more reasons below:
-
Pressure to “show progress” without a defensible baseline
-
Conflicting interpretations of DoD ZTA COA
-
Roadmaps built on opinion, not quantified maturity
-
Gaps discovered late in audits/ATOs/recompete
-
Leadership gets slides instead of numbers
The Offer: Zero Trust Progress Tracker
Zero Trust Progress Tracker
This is a productized, time‑boxed engagement, typically completed in 10–12 weeks. It is a single‑program fixed‑scope engagement that answers three questions:
-
Where do we actually stand today in our Zero Trust maturity?
-
What should we prioritize, and in what order?
-
What level of effort is required for each step so we can plan realistically?
Outcomes for your organization:
-
Defensible baseline against the DoD ZTA COA across all relevant pillars
-
COAaligned roadmap with clear sequencing, dependencies, and stopgates
-
Effort and impact ratings by phase
-
Stakeholder alignment around a single narrative: where we are, where we’re going, and why
-
Reduced delivery and contract risk by surfacing hidden blockers early (identity, data, segmentation, etc.)
-
A reusable, structured Phase 1 you can position on multiple programs instead of ad hoc workshops.
(pronounced EE-Zee, the French word for Easy)
AISE
STEP 1: ASSESS Where You Are
Use our comprehensive assessment questionnaire and automation tools to quickly and accurately determine where you are in your Zero Trust journey.
STEP 2: IDENTIFY Your Course
Rely on our experience and expertise to identify your best course of action based on the results of the assessment and the tools you already have in-house.
STEP 3: STRATEGIZE Your Moves
Strategize with us to achieve quick wins, repeatable results, and minimal disruption, following the Pareto Principle always holds.
STEP 4: EXECUTE Your Plan
Execute your plan. Together we take one step at a time, track our progress, celebrate our wins. Nothing succeeds like success.
AISE
How It Works (Timeline)
Phase 1
Discovery & Scoping
(Weeks 1–2)
-
Kickoff with executive sponsor and core team (prime + customer as needed)
-
Confirm scope and boundaries (programs, environments, pillars)
-
Identify stakeholders and existing artifacts
Phase 2
Data CollectioN
(Weeks 3–6)
-
Structured assessment sessions across Zero Trust pillars
-
Targeted SME interviews (tools, identity, network, data, etc.)
-
Evidence review to reduce subjective scoring
Phase 3
Analysis & Roadmap
(Weeks 7–9)
-
Maturity scoring by pillar and capability
-
Gap and dependency analysis
-
Prioritized roadmap with sequencing rationale, and effort and impact ratings
Phase 4
Synthesis & Readouts
(Weeks 10–12)
-
Draft findings review with working team
-
Executive briefing for leadership (prime and/or agency)
-
Technical deep dive for architects and implementers
Typical time investment:
-
Exec sponsor ~3–4 hours
-
Core team (2–4 people) ~15–20 hours
-
SMEs 1–2 hours each
What You Receive (Deliverables)
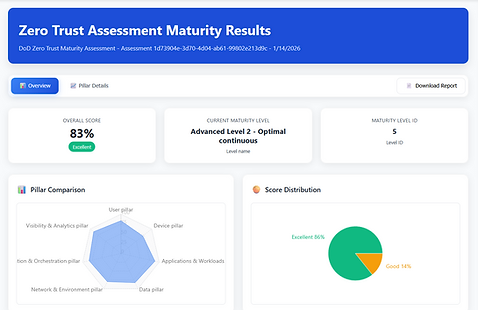
Scorecard
Zero Trust Maturity Scorecard – current posture by pillar/capability.
Gap Analysis
Where you fall short of target posture, with explicit dependencies.
Roadmap & Progress
Prioritized, sequenced steps – what to do first/next/later and why. Maturity levels over time.
Effort & Impact Ratings
Relative effort/impact per initiative to plan realistically and maximize ROI.
Executive Summary Deck
20‑minute leadership brief you can put in front of stakeholders

Clarity Guarantee
No one can credibly guarantee “compliance” or “no breaches.” What we do guarantee is clarity. If, after the final readout and deliverables, the leadership team does not feel materially clearer on:
-
Current Zero Trust posture,
-
Your top gaps and risks, and
-
The sequence and scale of effort required,
We will:
-
Provide up to two additional working sessions (up to 4 hours total) to refine, re-prioritize, or clarify the roadmap, and
-
Revise any deliverable sections that are not actionable enough
…at no additional cost.
The intent is simple: you walk away with a package you can act on and defend, not a report that sits on a shelf.
FAQs
-
Can this be run through our existing prime?
-
Yes
-
-
What if we’ve already done a Zero Trust assessment?
-
Excellent. We can import your assessment results into our system and you can then track progress going forward.
-
-
What’s required from our internal teams?
-
A few dedicated hours from SMEs per Pillar and Capability
-
-
Do you recommend or resell specific tools?
-
Yes, but we try to make the most of what you already have and what gives you maximum impact.
-
Why Agencies and Primes Choose Zephon



-
IRS: Modern IGA for 110k+ users; passed GAO/FISMA/FedRAMP/TIGTA audits
-
SEC: Zero Trust maturity assessment and funded multi‑year roadmap
-
DLA: Legacy ICAM solution now future ready




If you have one program where Zero Trust expectations and timelines feel fuzzy, this assessment is built for that
Zephon is committed to protecting and respecting your privacy, and we’ll only use your personal information to provide the products and services you requested from us. From time to time, we would like to contact you about our products and services, as well as other content that may be of interest to you.

